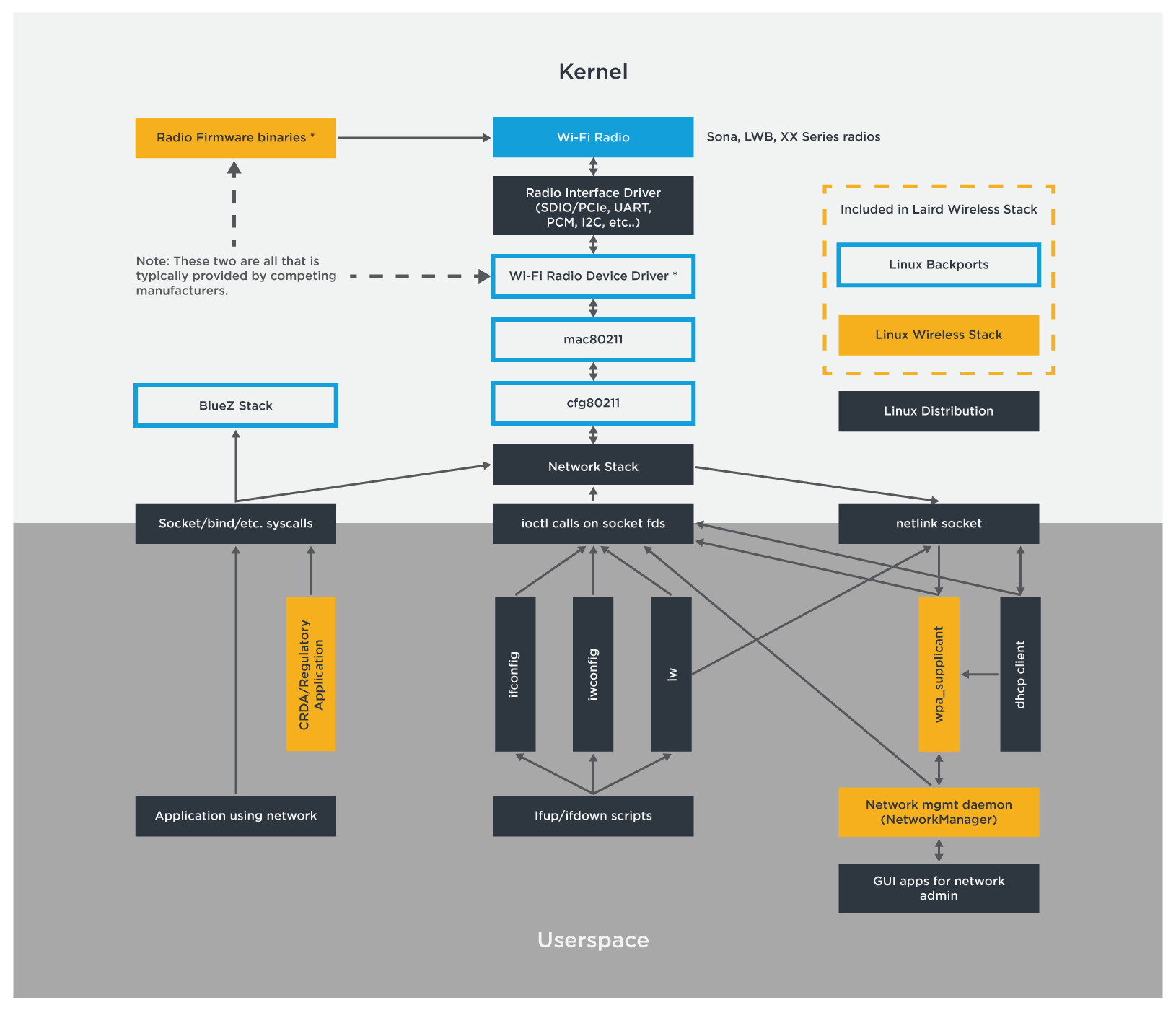
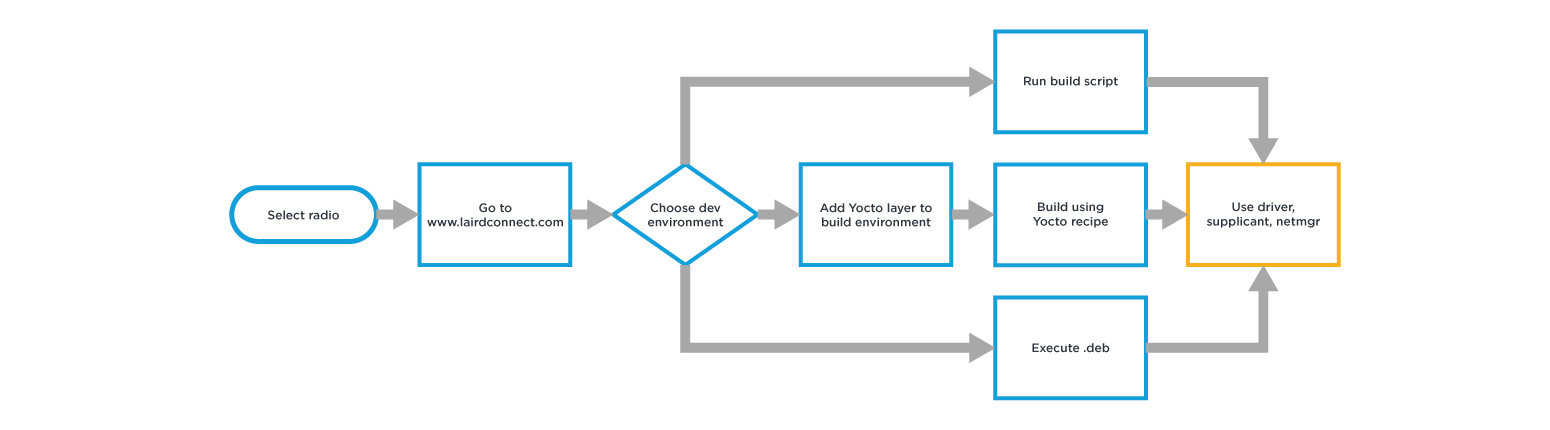
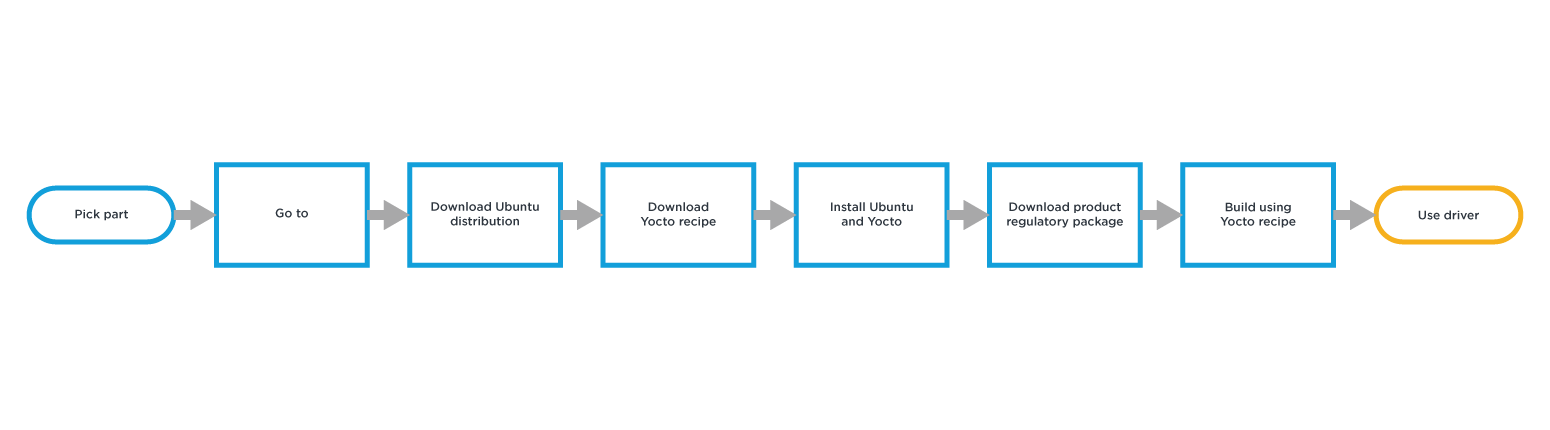
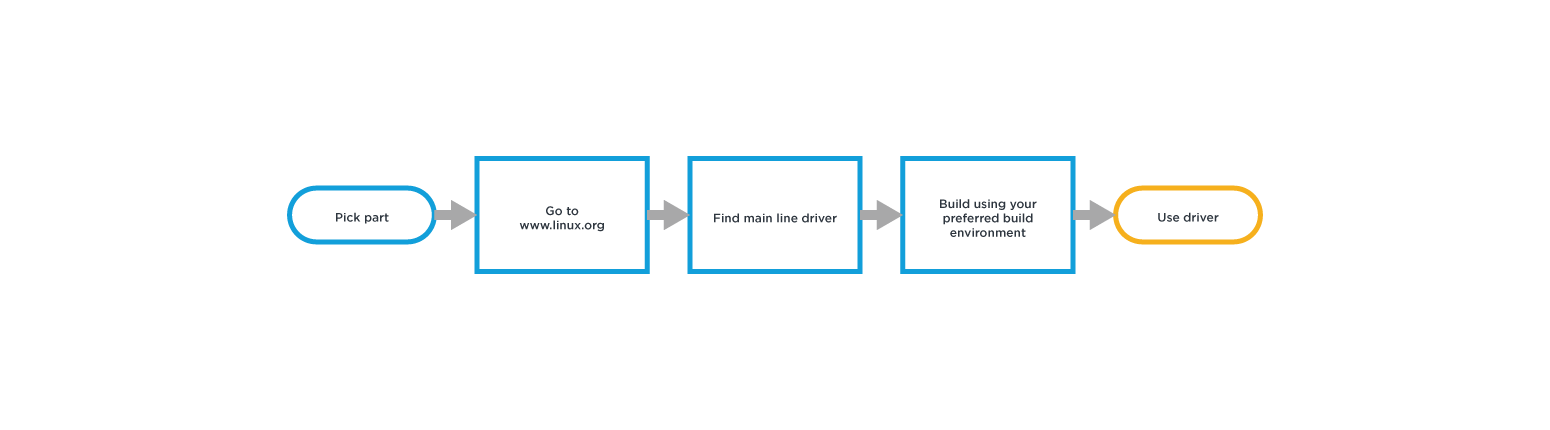
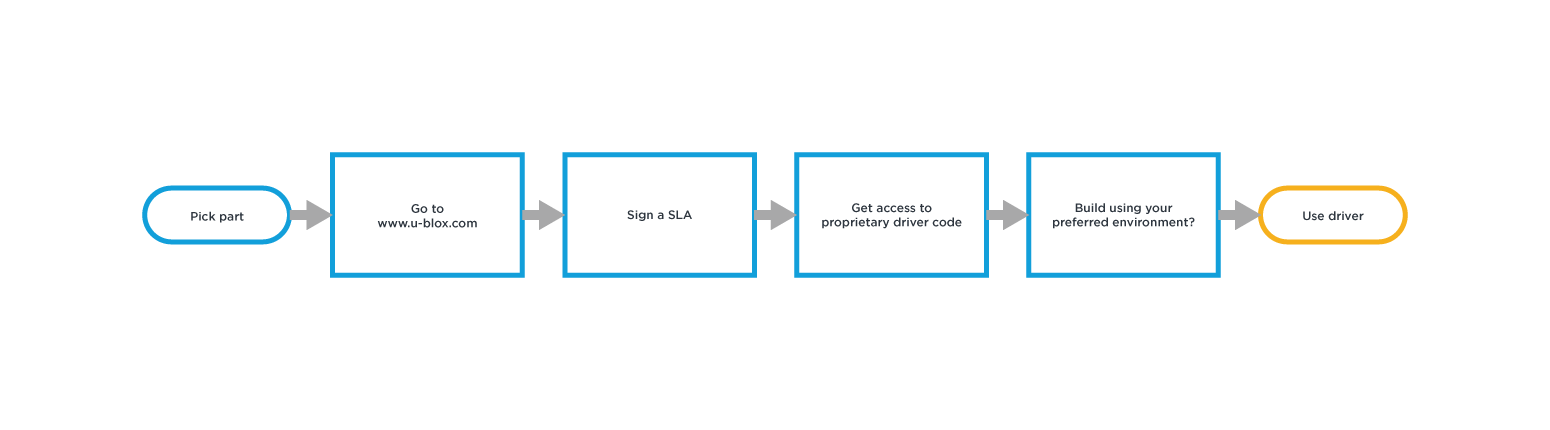
Option 2: Minimal Driver Support
This approach does mean there is now a known owner of the source code, although discussions around whether the module provider or the semiconductor manufacturer will own support remain.
With this approach it is possible to provide development system support e.g. Yocto specifically for the source being provided. Typically, only the build systems supported directly by the semiconductor manufacturer will be supported. This requires you to either change your build system to the one supported or work out how to port the available code into your build system and tool chain.
With this approach it is very likely that no additional testing of the code has been done, except to make sure in a limited configuration the driver will build. Support for multiple kernels and platforms is likely not to exist and therefore porting to your platform will fall on you or require additional effort and delays from the module vendor or 3rd party.
Making sure you have the best radio firmware and necessary regulatory binaries can be challenging as it will depend upon the module manufacturer (or the semiconductor manufacturer) to make sure these are made available for not only the silicon radio but the manufactured module.